OPENVPN Manual of Industrial Cellular Routers USR-G806
Overview
This manual introduces the industrial cellular routers USR-G806 OPENVPN Client function.
1. Introduction
OPENVPN is application layer VPN which bases on Openssl library. It supports bidirectional authentication which bases on certificate, that’s to say client needs to authenticate server and server also needs to authenticate client.
2. Configuration
2.1. Enter G806 Web Server
Connect PC to G806 LAN interface or WLAN interface and configure PC into DHCP mode as follow:
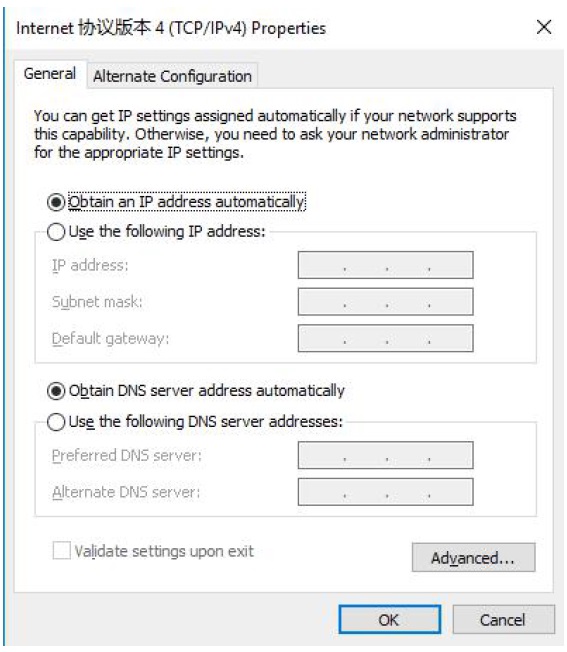
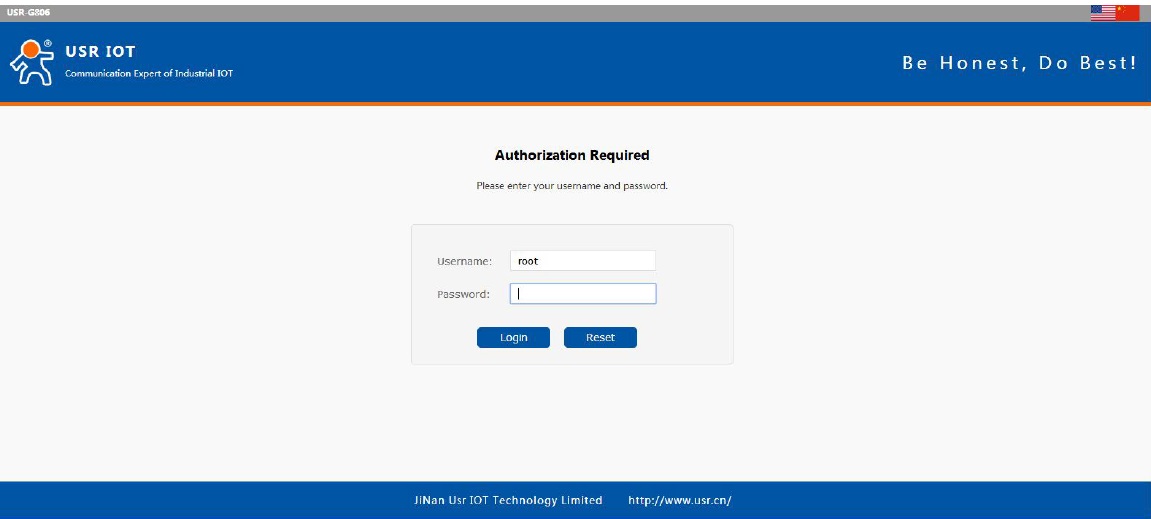
Then enter G806 Web Server by entering G806 LAN interface IP address (Default is 192.168.1.1) and login with username and password(Default both are root). User can switch between English/Chinese from top right corner.
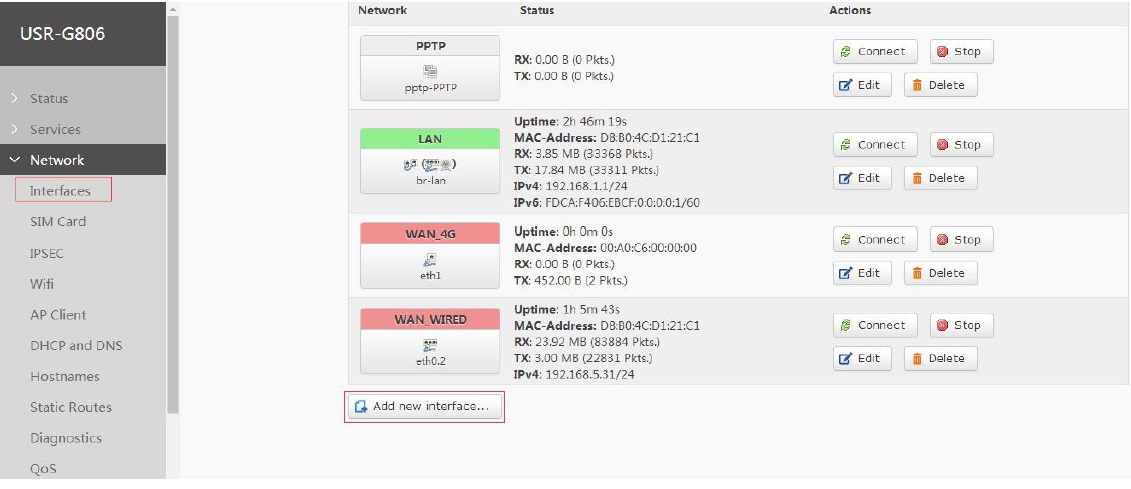
2.2. Add OPENVPN interface
After entering Web Server, add OPENVPN interface as follow:
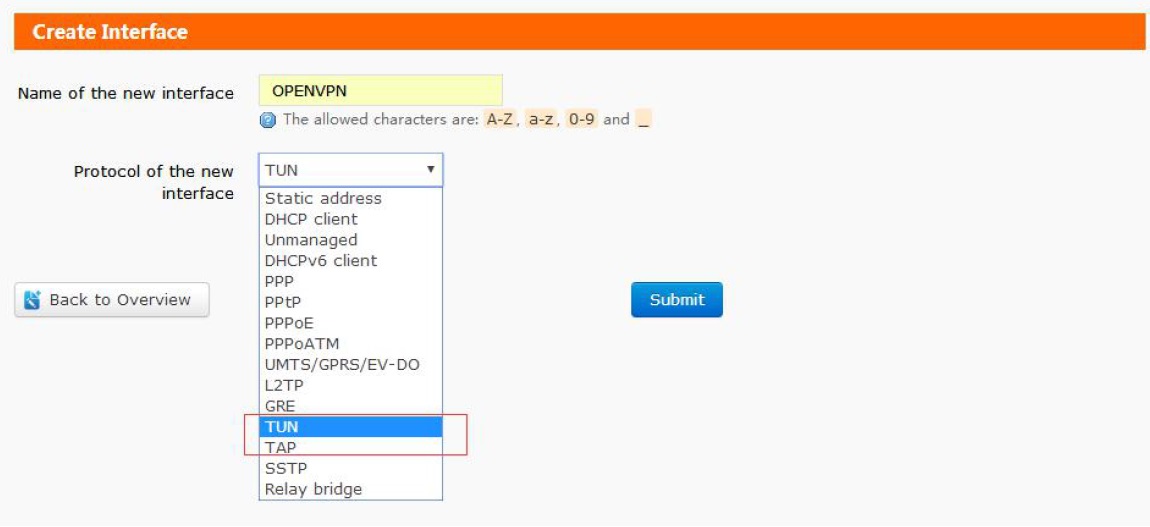
Protocol can be TUN(Route mode) or TAP(Bridge mode). After typing in interface name and choosing protocol, please click ‘Submit’ to add OPENVPN interface.
2.3. Configure OPENVPN interface
After adding OPENVPN interface, it will be OPENVPN interface configuration web page. Configure ‘General Setup’:
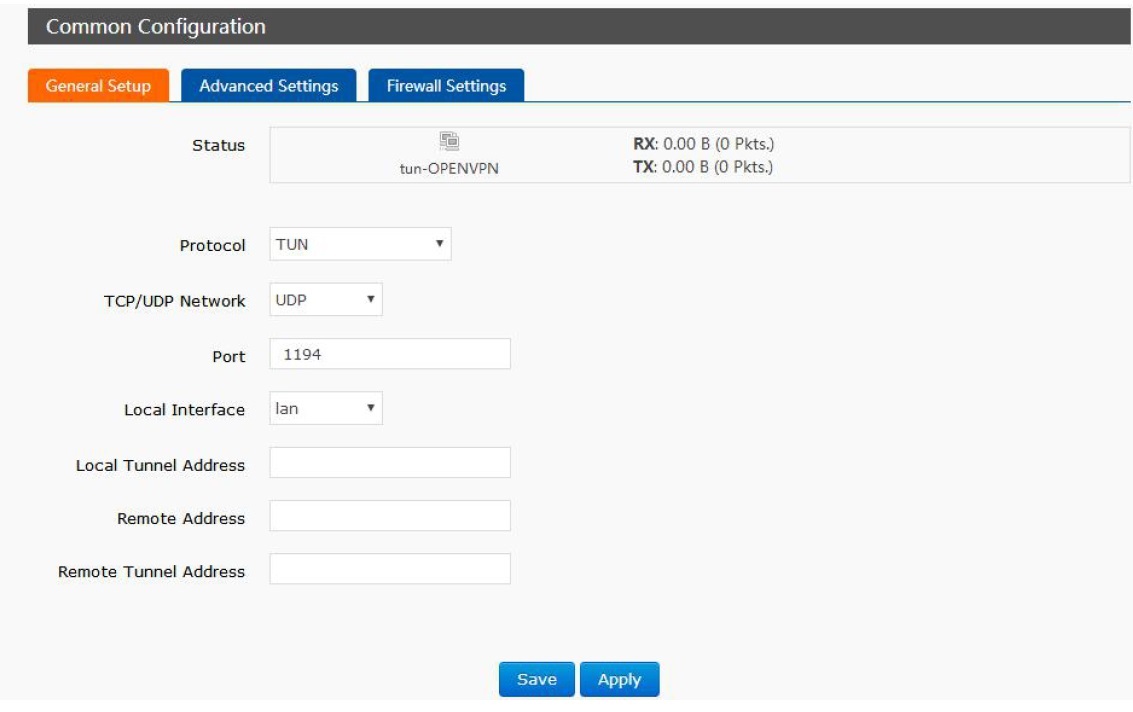
Protocol: Can choose TUN(Route mode) or TAP(Bridge mode).
TCP/UDP Network: Can choose UDP protocol or TCP protocol. Port: Listening port of OPENVPN Client.
Local Interface: Choose wan_wired or wan_4g according to how G806 accesses to network.
Local Tunnel Address: Server will automatically distribute if user don’t fill it.
Remote Address: Server IP or domain name.
Remote Tunnel Address: Server will automatically distribute if user don’t fill it.
After configuring ‘General Setup’ and clicking ‘Save&Apply’, please configure ‘Advanced Settings’:
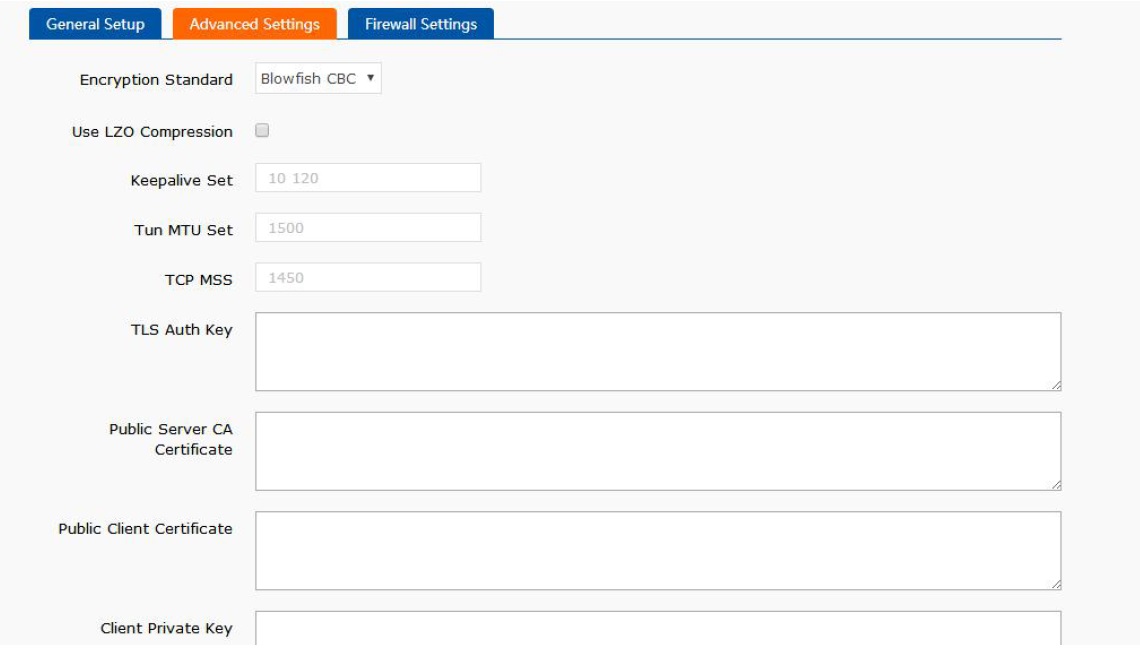
Encryption Standard: Include Blowfish CBC, AES-128 CBC, AES-192 CBC, AES-256 CBC, AES-512 CBC.
Use LZO Compression: User can check it to enable LZO Compression in data transmission.
Keepalive Set: Default is 10 120.
Tun MTU Set: Configure MTU value of tunnel.
TCP MSS: Maximum segmenting size of TCP data.
TLS Auth Key: Authentication key of Transport Layer Security.
Public Server CA Certificate: Public CA certificate of Server and Client.
Public Client Certificate: Client certificate.
Client Private Key: Client private key.
Note:
1. Before Client connecting to Server, Server should provide: CA certificate, Client certificate, Client private key, TLS authentication key.
2. After getting above certificates and keys, just copy them into corresponding edit box in ‘Advanced Settings’. After configuring ‘Advanced Settings’ and clicking ‘Save&Apply’, OPENVPN interface has finished configuring.
